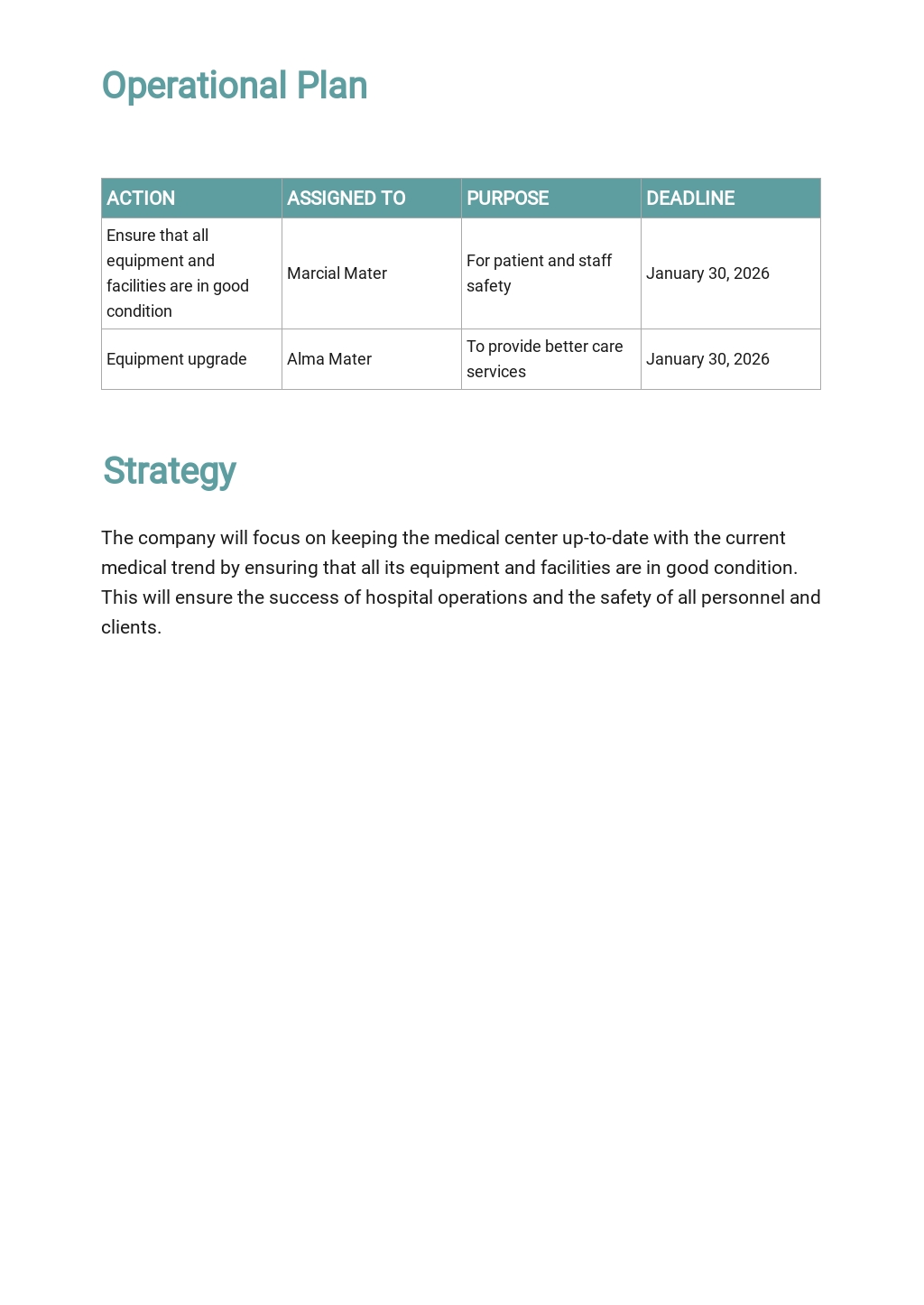
Vulnerability Management Plan Template - This guide is intended for organizations seeking help in establishing a vulnerability management process. Free threat & vulnerability management templates for organizations to effectively identify and mitigate security risks internally. This policy template is meant to supplement the cis controls v8. Understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources. Start freeno credit card required Learn how to define the scope, carry out vulnerability scanning, prepare. The process areas described include •. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and processes to incorporate security controls. A guide for systematic detection, mitigation, and review of risks. This vulnerability management plan template provides a structure and guidance to help create a comprehensive plan that identifies and mitigates security risks, threats, and other.
Vulnerability Assessment Plan Template in Word, Pages, Google Docs
This vulnerability management plan template provides a structure and guidance to help create a comprehensive plan that identifies and mitigates security risks, threats, and other. This guide is intended for organizations seeking help in establishing a vulnerability management process. A guide for systematic detection, mitigation, and review of risks. The process areas described include •. Free threat & vulnerability management.
Vulnerability Management Program Template Stcharleschill Template
The process areas described include •. This policy template is meant to supplement the cis controls v8. A guide for systematic detection, mitigation, and review of risks. Understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources. Start freeno credit card required
Fresh Vulnerability Management Program Template Sparklingstemware
Start freeno credit card required This guide is intended for organizations seeking help in establishing a vulnerability management process. A guide for systematic detection, mitigation, and review of risks. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and processes to incorporate security controls. This vulnerability management plan template provides a structure and guidance to.
Fantastic Vulnerability Management Program Template Sparklingstemware
The process areas described include •. This vulnerability management plan template provides a structure and guidance to help create a comprehensive plan that identifies and mitigates security risks, threats, and other. A guide for systematic detection, mitigation, and review of risks. This policy template is meant to supplement the cis controls v8. Understanding and managing vulnerabilities is a continuous activity,.
Vulnerability Reporting Template
This policy template is meant to supplement the cis controls v8. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and processes to incorporate security controls. This guide is intended for organizations seeking help in establishing a vulnerability management process. Understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources..
Key Elements Of Vulnerability Administration Plan Sample PDF
Start freeno credit card required A vulnerability management policy defines an approach for vulnerability management to reduce system risks and processes to incorporate security controls. Free threat & vulnerability management templates for organizations to effectively identify and mitigate security risks internally. Understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources. The process areas described.
Vulnerability Management Process Template
This guide is intended for organizations seeking help in establishing a vulnerability management process. Understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and processes to incorporate security controls. Start freeno credit card required A guide for systematic detection, mitigation,.
Creating a Vulnerability Management Strategy zSecurity
The process areas described include •. Start freeno credit card required This policy template is meant to supplement the cis controls v8. Learn how to define the scope, carry out vulnerability scanning, prepare. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and processes to incorporate security controls.
Vulnerability Management Plan Template
Understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources. This vulnerability management plan template provides a structure and guidance to help create a comprehensive plan that identifies and mitigates security risks, threats, and other. A guide for systematic detection, mitigation, and review of risks. A vulnerability management policy defines an approach for vulnerability management.
Vulnerability Management Template
Start freeno credit card required The process areas described include •. Understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources. This vulnerability management plan template provides a structure and guidance to help create a comprehensive plan that identifies and mitigates security risks, threats, and other. Learn how to define the scope, carry out vulnerability.
This vulnerability management plan template provides a structure and guidance to help create a comprehensive plan that identifies and mitigates security risks, threats, and other. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and processes to incorporate security controls. Start freeno credit card required Learn how to define the scope, carry out vulnerability scanning, prepare. A guide for systematic detection, mitigation, and review of risks. This guide is intended for organizations seeking help in establishing a vulnerability management process. The process areas described include •. Free threat & vulnerability management templates for organizations to effectively identify and mitigate security risks internally. Understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources. This policy template is meant to supplement the cis controls v8.
This Guide Is Intended For Organizations Seeking Help In Establishing A Vulnerability Management Process.
The process areas described include •. This vulnerability management plan template provides a structure and guidance to help create a comprehensive plan that identifies and mitigates security risks, threats, and other. This policy template is meant to supplement the cis controls v8. Understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources.
Start Freeno Credit Card Required
Free threat & vulnerability management templates for organizations to effectively identify and mitigate security risks internally. Learn how to define the scope, carry out vulnerability scanning, prepare. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and processes to incorporate security controls. A guide for systematic detection, mitigation, and review of risks.